AKASHA Core: Decentralized Identifiers 101 (DIDs)
Tired of the pitfalls of traditional identity models? Imagine a world where you own your online identity, free from centralized control and the constant threat of data breaches. This is the promise of Decentralized Identifiers (DIDs).

The internet's been a cool, wild ride, but traditional centralized identity systems have left us exposed and vulnerable. Enter Decentralized Identifiers (DIDs) – the game-changing solution we've all been waiting for. With DIDs, we can reclaim control over our digital identities, ensuring security and interoperability like never before. In this piece, we'll explore the flaws of old-school identity models, the evolution and mechanics of DIDs, and how AKASHA is pioneering their use through AKASHA Core and AKASHA World.
Digital identity: the manifestations and operations of human identity influenced or mediated by digital technology (from the AKASHA Glossary)
The Internet Before DIDs: The Identity Crisis
Still today, the internet operates on a centralized identity model fraught with serious flaws. Users don't own their identifiers—emails, usernames, you name it. These are controlled by service providers who can revoke or alter them on a whim. Imagine investing years into building your online persona only to have it wiped out because of a policy change. This lack of ownership disempowers users and makes their online presence precarious, especially in an era where many depend on their online identity to earn a living.
Adding fuel to the fire, centralized storage systems remain prime targets for hackers. A single breach can expose millions, if not billions, of accounts, as seen in the 2013 Yahoo data breach and the Facebook-Cambridge Analytica scandal.
Privacy, meanwhile, continues to be a major casualty. Service providers collect extensive data without user consent, monetizing it through targeted advertising. Giants like Google and Facebook thrive on this model, selling user data, raising serious ethical concerns, and leaving users vulnerable to privacy violations and data exploitation.
As if that weren't enough, the fragmentation of digital identities adds to the chaos. Users must manage multiple accounts with different usernames and passwords. This cumbersome process often results in weak or reused passwords, further compromising security.
Centralized control also means users have little say in how their data is used. Service providers dictate terms, prioritizing corporate interests over individual rights and freedoms. This imbalance leaves users at the mercy of policies that often disregard their privacy and autonomy.
All these limitations underscore the urgent need for a decentralized, user-centric approach to digital identity management. Enter DIDs.

The Rise of DIDs: Why They Matter
The concept of Decentralized Identifiers (DIDs) emerged in the mid-2010s as part of a broader movement towards decentralization and user sovereignty in the digital world. The idea of decentralized identity gained traction alongside the rise of blockchain technology. Early pioneers, such as Vitalik Buterin with Ethereum, envisioned a future where users could control their digital identities without relying on centralized authorities.
Blockchain Influence
The blockchain community recognized early the need for a new identity model. The immutable and decentralized nature of blockchain technology provided the perfect foundation for this new model:
- Permanence: DIDs are persistent identifiers that do not need to change over time.
- Resolvability: They can be looked up to obtain metadata, ensuring they are usable across various contexts.
- Cryptographic verifiability: DIDs use cryptographic methods to prove ownership and control, thus enhancing security.
- Decentralization: Unlike traditional identifiers, DIDs do not rely on a centralized registration authority, reducing the risk of central points of failure.
Various blockchains and entities have implemented their own DID methods, showcasing the versatility and potential of DIDs:
- PKH (Public Key Hash): Commonly used in platforms like Bitcoin and Ethereum, PKH-derived DIDs allow users to interact with blockchain networks securely, verifying transactions and ownership without exposing the actual public key.
- ED25519: This DID uses the Ed25519 public key signature system, known for its cryptographic strength and efficiency. It's widely adopted in decentralized systems for secure and fast digital signatures.
- Sovrin Network: Sovrin manages self-sovereign identities on its blockchain, allowing users to create DIDs and use them to issue and verify verifiable credentials, such as academic qualifications.
- Microsoft ION: Built on the Bitcoin blockchain, ION is a decentralized identity layer that enables the creation and management of DIDs. It uses a distributed, permissionless network to ensure users have full control over their identities.
Standardization Efforts and the W3C
In 2017, the World Wide Web Consortium (W3C) initiated the Decentralized Identifier Working Group. This group aimed to create a standardized framework for DIDs, ensuring they could be universally adopted and implemented. Their efforts culminated in the publication of the DID Core Specification, which outlines the architecture, data model, and methods for implementing DIDs.
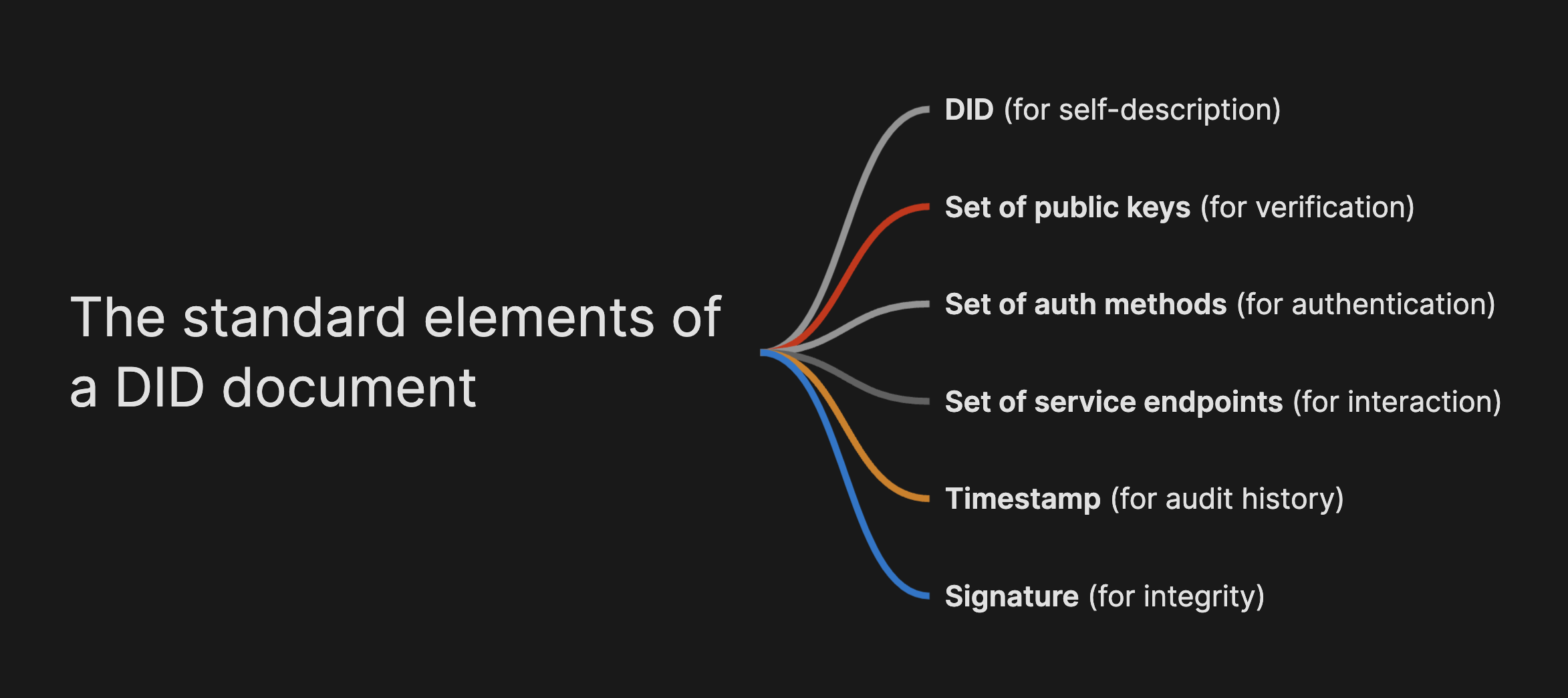
How DIDs Work: A Closer Look
Here's a step-by-step process to understand how DIDs work.
Step 1: Create a DID
- Anyone can generate a DID without needing permission from a central authority. This process is typically done using cryptographic methods, ensuring that each DID is unique and secure.
- Example: A user creates a DID using a blockchain-based wallet like MetaMask or 3box, which generates a unique cryptographic key pair (public and private keys).
Step 2: Associate a DID Document
- Each DID is associated with a DID document. This document includes metadata about the DID, such as public keys, authentication methods, and service endpoints.
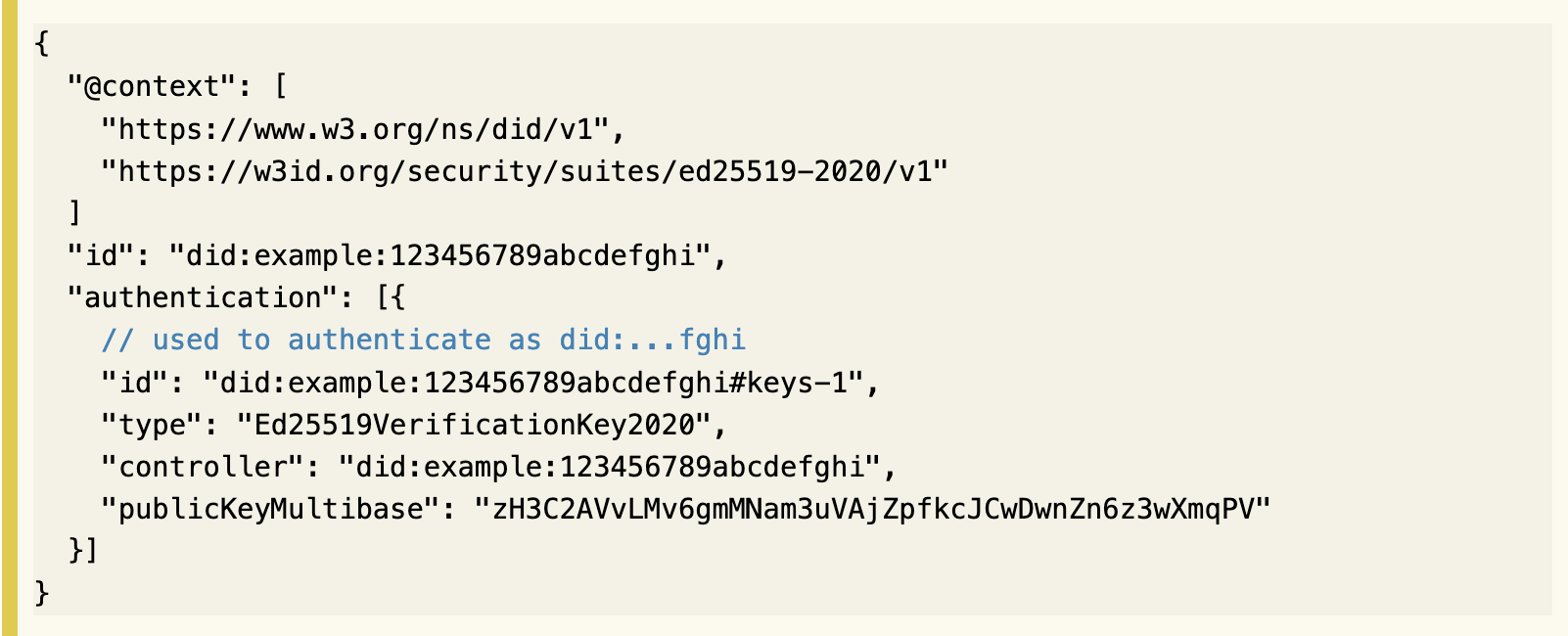
Step 3: Store the DID Document on Decentralized Networks
- Decentralized Storage: The DID document is stored on a decentralized network, such as a blockchain or the InterPlanetary File System (IPFS).
Step 4: Resolve the DID
- When a DID needs to be resolved, meaning the associated DID document needs to be retrieved, a decentralized resolution process is used. This typically involves querying a blockchain or distributed ledger to find the document.
Step 5: Verify and Manage the DID
- Users have full control over their DIDs. They can update their DID documents to rotate keys, add new service endpoints, or even revoke the DID if needed.
- Example: If a user believes their private key is compromised, they can update their DID document to reflect a new public key, ensuring continued security.
Modular Magic: AKASHA Core and DIDs
AKASHA Core is the open-source framework for building and distributing composable web3 apps. It integrates DIDs to ensure secure, tamper-proof, and user-owned data management. Central to this system is Ceramic, which acts as the backbone for decentralized data handling. More specifically, Ceramic streams act as the ever-vigilant guardians of your data, using an account model for authentication and authorization.
Supported DID methods in Ceramic offer flexibility and strength for different needs:
- PKH DID: Perfect for blockchain accounts, these DIDs are created from blockchain addresses, making it easy to sign, authorize, and authenticate within DID-based environments.
- Key DID: This method turns a cryptographic public key into a DID Document, supporting key types like Ed25519 and Secp256k1. While Key DIDs aren't usually for long-term use, they're great for short-lived identities.
For developers, AKASHA Core offers a robust framework that empowers them to build applications with a strong focus on user autonomy. By integrating DIDs, devs can ensure their apps provide secure, decentralized data management, making their projects more trustworthy and resilient.
DIDs in AKASHA World: Connect On Your Terms
Just as AKASHA Core empowers developers, AKASHA World empowers users with a web3-powered social platform that honors your right to a universal digital identity. It leverages DIDs to provide a flexible and secure method of login and identity verification.
Users can authenticate using their own identity method or create a portable profile that will travel with them across the web3 ecosystem:
- Sign-In with Ethereum: It's a decentralized authentication method that leverages the Ethereum blockchain to allow users to log in to websites or applications using their Ethereum wallet. This method provides a secure and private way to authenticate without relying on traditional centralized identity providers like Google or Facebook. Users can sign in using their Ethereum Name Service (ENS) name, which acts as a human-readable DID pointing to their Ethereum address.
- Cross-Chain Identity: AKASHA World supports identifiers from various chains (e.g. Solana), offering a cross-chain identity solution. This ensures users aren’t limited to a single blockchain or identity provider, boosting interoperability within the web3 ecosystem.
Connect on your terms on AKASHA World
Users maintain full control over their identity and personal data, reducing the risk of data breaches and unauthorized access. DIDs let them decide how they present themselves online and who has access to their information, allowing them to manage their digital presence with complete autonomy.
👉 DID systems significantly enhance security, but they're not entirely immune to data breaches. Key management is crucial, as poor handling can lead to unauthorized access. Also, keep an eye out for software vulnerabilities and social engineering tactics, which can pose risks, along with any weaknesses in smart contracts. Embracing DID systems means staying vigilant and practicing robust security measures to unlock their full potential without compromising user safety.
Let's face it – centralized identity systems have let us down. DIDs are the future, and AKASHA is spearheading this movement by putting users back in control. With DIDs, your digital identity is secure, private, and interoperable across platforms. It's time to ditch the old ways and enter a world where you own your identity. AKASHA is making this possible, and there's never been a better time to get on board.
Don't hesitate to reach out on our Discord server or Twitter!

